SECURITY CONSULTING
of IT Security
Detect the Cyberthreats with Ease
Being one of the top security consulting service providers, Exigo Tech offers customised and innovative end-to-end IT security solutions by reviewing your existing architecture to detect vulnerabilities and identify gaps. We keep improving your existing security policies and offer advice to roll out a secured infrastructure from scratch.
Security Strategy
Security Standards
Maturity Assessment
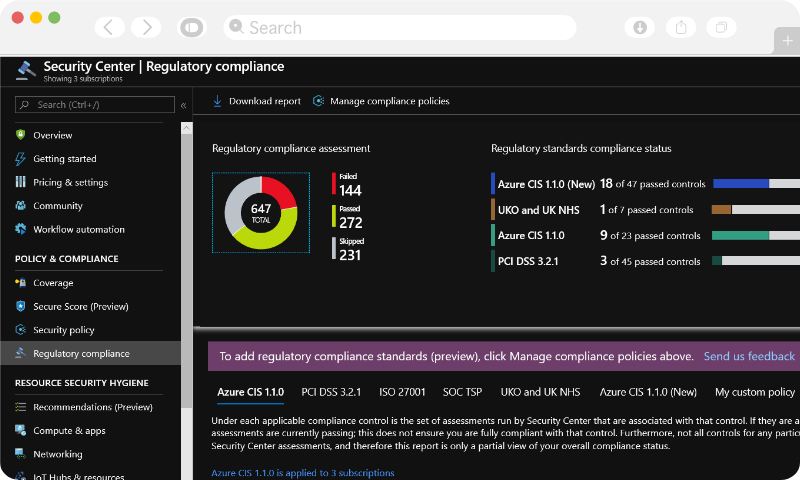
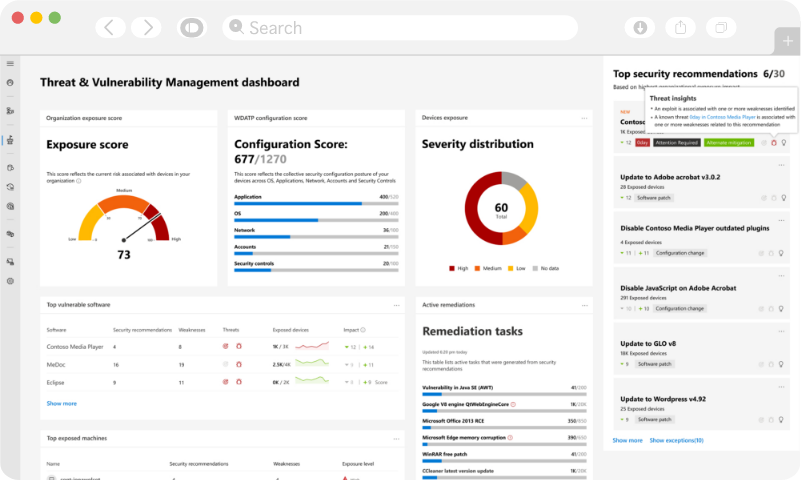
Security Dashboards
Executive Briefings
Security Trusted
Advisor

![]()
“Our association with Exigo Tech enabled us to automate our manual HR processes to improve our productivity and efficiency levels. The Exigo Tech team listened to our needs carefully and followed a step-by-step approach to implementation.”

“Exigo Tech was instrumental in designing and implementing our WAN infrastructure. They catered to our requirements after understanding our specific needs.”

“Exigo Tech created a highly complicated logistics platform for us, that enabled us to manage the entire logistics process properly. We have benefitted from their flawless and detail-oriented approach.”
![]()
“Rhino Rack has gained a trusted advisor in Exigo Tech to advise and assist with all of our business requirements. We are looking forward to continuing our relationship with Exigo Tech.”

“Cenversa has been working with Exigo Tech to move the file server and intranet to the cloud. They came up with a secure and scalable customer and supplier centric architecture in a structured format.”

“Exigo Tech is highly recommended from the Polyseal Group for all your IT requirements. They listened to our requirements carefully and delivered solutions to increase our productivity and end user experience.”
“We liked Exigo Tech’s clear understanding of what needs to be achieved and knowing ways to improve the user experience in building custom applications for us.”





LATEST THINKING
 Singapore
Singapore Philippines
Philippines India
India Australia
Australia Singapore
Singapore Philippines
Philippines India
India