CLOUD SECURITY
Build Highest Standards
of Cloud Security
Integrate cloud computing security into every step of your cloud journey to maximise business growth
Enable a Faster, Stronger, Secure Cloud Computing Environment
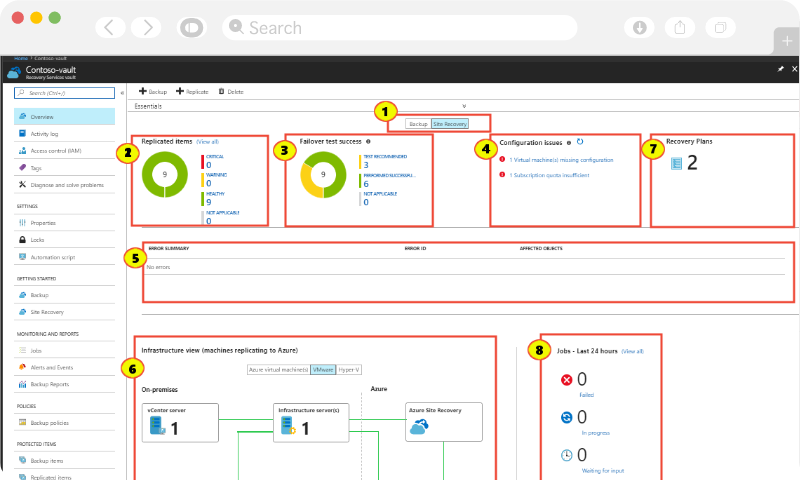
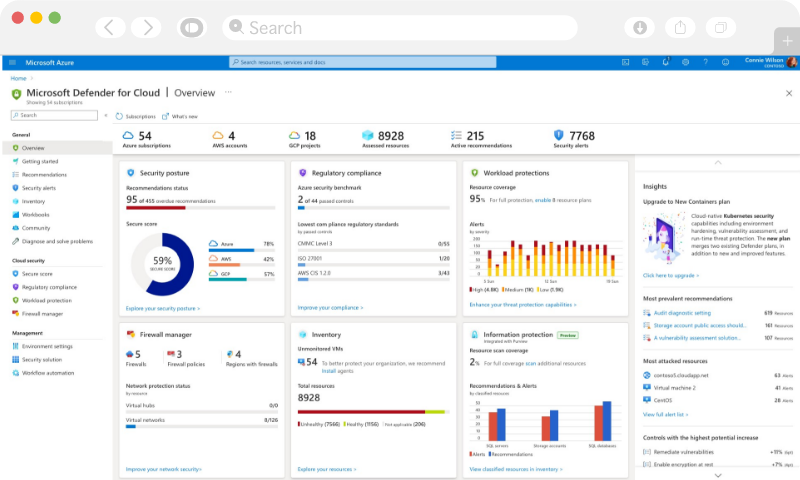
As enterprises turn to multiple cloud solutions, they also face new risks and added responsibilities to maintain strong cloud security. Cloud security also known as cloud computing security involves formulating strategies and policies to protect the data and infrastructure with regards to the cloud. Several security concerns such as data breaches, hacked interfaces, compromised credentials, and system vulnerabilities often lead to devastating effects. Exigo Tech helps you to overcome these security concerns by providing cloud services in a secure manner with complete support.
We help businesses to build secure cloud-first capabilities complying with industry regulations and security standards.
ELEVATE YOUR CLOUD SECURITY
Protect your data, applications, and infrastructure that are involved within the public, private or hybrid cloud with our cloud computing security solutions to make the system function easily.

Identity Protection
Public Cloud
Security
Cloud Compliance Solutions
Business Continuity
and Disaster Recovery
Cloud CRM/ERP Solutions

![]()
“Our association with Exigo Tech enabled us to automate our manual HR processes to improve our productivity and efficiency levels. The Exigo Tech team listened to our needs carefully and followed a step-by-step approach to implementation.”

“Exigo Tech was instrumental in designing and implementing our WAN infrastructure. They catered to our requirements after understanding our specific needs.”

“Exigo Tech created a highly complicated logistics platform for us, that enabled us to manage the entire logistics process properly. We have benefitted from their flawless and detail-oriented approach.”
![]()
“Rhino Rack has gained a trusted advisor in Exigo Tech to advise and assist with all of our business requirements. We are looking forward to continuing our relationship with Exigo Tech.”

“Cenversa has been working with Exigo Tech to move the file server and intranet to the cloud. They came up with a secure and scalable customer and supplier centric architecture in a structured format.”

“Exigo Tech is highly recommended from the Polyseal Group for all your IT requirements. They listened to our requirements carefully and delivered solutions to increase our productivity and end user experience.”
“We liked Exigo Tech’s clear understanding of what needs to be achieved and knowing ways to improve the user experience in building custom applications for us.”





LATEST THINKING
Monday to Friday | 9am to 5pm (AEST)
Monday to Friday | 9am to 5pm (AEST)
 Singapore
Singapore Philippines
Philippines India
India Australia
Australia Singapore
Singapore Philippines
Philippines India
India