Because of the recent instances in 2020, you could say that the chief information security officers (CIO) never seem to get a break. During the first quarter, they had to ensure that their organisation is equipped with apt infrastructure to support the need for the work from home scenario and this was quickly followed by a cyber-attack. Increasing security risks, business continuity challenges, new rules and regulations mandated by the federal government are some of the things that always keep CIOs on their toes. In this blog post, I will talk about several measures and network security practices which organisations can follow to allow their CIOs to have a breather and somewhat raise the bar of the security for their intellectual properties.
Network Security Practices – A Bunch of Tried and Tested Techniques to Reduce the Possibilities of Data Theft
Australian businesses of every vertical and size whether they are a government organisation or a private agency need to adapt the latest security techniques, conduct regular training for their employees and incorporate new technologies such as artificial intelligence and machine learning in their cybersecurity strategies to keep themselves a step ahead from the hackers.
-
Ensure collaboration between the teams
Bringing all the required departments on the same page and breaking silos between them has its upside. The organisations having a continuous flow of information between the networking and security teams face fewer breaches. And if there are attacks, these have less impact on the business continuity and finances.
-
Implement zero trust framework
The Bring Your Own Device (BYOD) concept and work from home scenario have introduced several challenges which are quite difficult to overcome. I recommend the implementation of a zero-trust security model wherein all the devices are protected with multi-factor authentication and other methods. You can use the below mentioned steps to formulate a zero-trust framework. 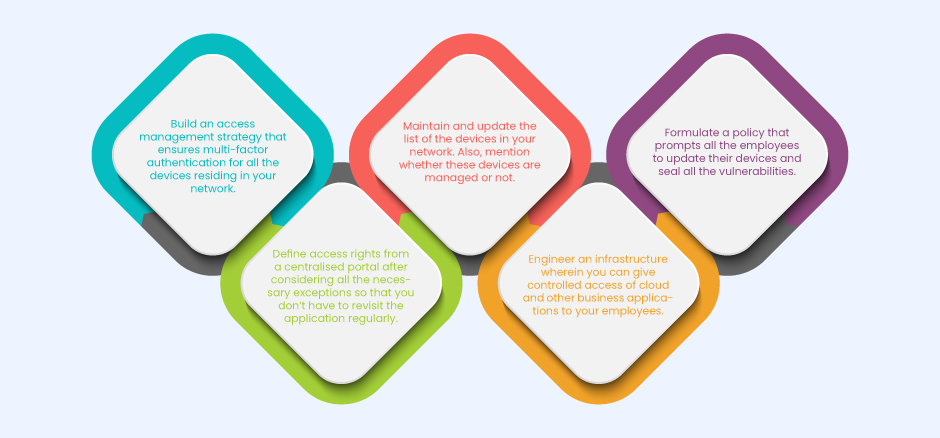
-
Verify security controls and audit the network resources
The knowledge about the network’s status plays a critical role in enabling you to control or tighten your network security. You should be conducting an audit of network resources regularly to identify the loopholes in the infrastructure and seal them before any intrusion occurs. You can identify the unused or old applications residing in your business ecosystem and remove them to ensure network high performance. Security audits are considered to be one of the best network security practices because you get to know the status of server backups and collate all the information required to formulate disaster recovery plans.
-
Update and circulate the security policies regularly
In many conditions it happens that while addressing the current needs, businesses fail to update their security policies. More often than this, businesses forget to communicate their updated policies to their teams. Both of these practices pave a path for bad actors to enter your network. Therefore, make it a point that you periodically check the security policies, update them whenever required and share it with the relevant professionals so that if there is a breach the employees can take immediate remedial action and reduce its impact. 
-
Upgrade and update antimalware applications
Updating the antimalware applications is one of the ideal network security practices. You need to make it mandatory for the security and networking teams to regularly check the antimalware applications for any updates. You should get the patch management automated to shield your digital properties.
-
Define and standardise security procedures
Security is a continuous process and relentless efforts are required to ensure its healthy state. Therefore, it is ideal to have a process in place wherein you and your employees are prompted to monitor the network resources and adjust them if need be.
Tailor your Network Security Practices with US!
One critical requirement to ensure the security of the infrastructure is a disciplined approach wherein you and your teams strive to check the imperatives and remain updated about the new threats or hacking methods. You and your team need to upgrade yourselves with the latest mitigation methods and learn from past attacks and implement that knowledge to protect the future breaches.
You can outsource the security aspect of your business to us to find more time to focus on strategic initiatives and product development. We are a Sophos Platinum partner and hence our team is always updated about the latest network security practices and can implement the same for you to enhance your security posture. Let’s get associated to uplift the security quotient of your organisation!
 Singapore
Singapore Philippines
Philippines India
India Australia
Australia Singapore
Singapore Philippines
Philippines India
India Vivek Trivedi | Aug 20, 2020
Vivek Trivedi | Aug 20, 2020









