SECURITY | INFRASTRUCTURE SECURITY
SECURITY
INFRASTRUCTURE SECURITY
Prepare Against Infrastructure Security Attacks
Improve the performance of your business by making the IT infrastructure secure
Strengthen your Network and Infrastructure with Modern Solutions
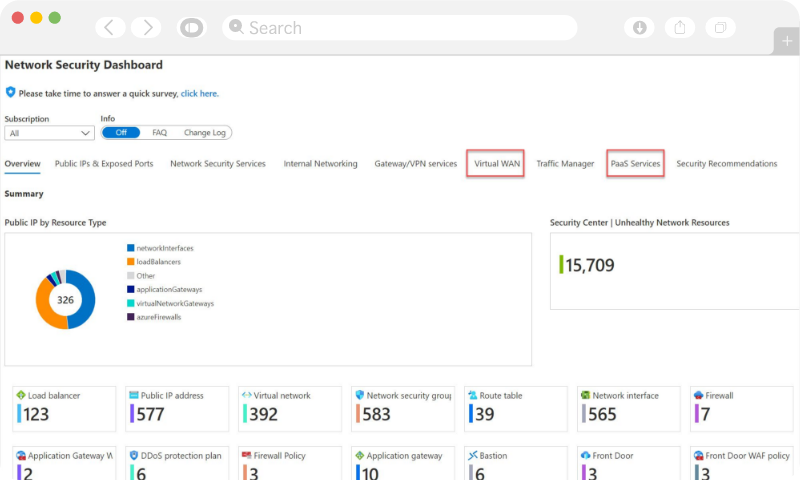
With remote working becoming the new norm, securing access identities and interfaces is necessary to maximise the benefits of the cloud. A zero-trust strategy is the need of the hour for cloud enterprises nowadays. Exigo Tech’s cloud infrastructure security services enable secure access to the cloud by protecting your environment from security threats.
We build security at every level of your IT infrastructure while providing continuous intelligence, monitoring and support for the improvement and better management of your security landscape. Our infrastructure security solutions recommend you the best security strategies and help you access security and compliance practices.
OPTIMISE IT INFRASTRUCTURE
We offer infrastructure security solutions to cover all the aspects of security from identity to access to an app, data, and network to improve productivity.
Manage People
Risks
Bring together the people, process, and technology to achieve resilience against rising threats to protect your modern enterprise against internal and external vulnerabilities.
Mobile Device
Management
Our mobile device management solutions allow your IT admins to control security policies for the devices accessing sensitive data.
Wireless Security
Infrastructure security solutions like wireless LAN network monitor and act upon the health status of connected endpoints to reduce the risk to your trusted network.
Protect Computer
and Networks
Secure your computer networks from malicious attacks from intruders and focus on keeping them free of future threats.
Firewall Solution
We offer advanced threat-focused next-generation firewalls to put a barrier between your untrusted outside networks and trusted internal networks to protect your organisation’s network.

![]()
“Our association with Exigo Tech enabled us to automate our manual HR processes to improve our productivity and efficiency levels. The Exigo Tech team listened to our needs carefully and followed a step-by-step approach to implementation.”

“Exigo Tech was instrumental in designing and implementing our WAN infrastructure. They catered to our requirements after understanding our specific needs.”

“Exigo Tech created a highly complicated logistics platform for us, that enabled us to manage the entire logistics process properly. We have benefitted from their flawless and detail-oriented approach.”
![]()
“Rhino Rack has gained a trusted advisor in Exigo Tech to advise and assist with all of our business requirements. We are looking forward to continuing our relationship with Exigo Tech.”

“Cenversa has been working with Exigo Tech to move the file server and intranet to the cloud. They came up with a secure and scalable customer and supplier centric architecture in a structured format.”

“Exigo Tech is highly recommended from the Polyseal Group for all your IT requirements. They listened to our requirements carefully and delivered solutions to increase our productivity and end user experience.”
“We liked Exigo Tech’s clear understanding of what needs to be achieved and knowing ways to improve the user experience in building custom applications for us.”

![]()


![]()
LATEST THINKING
Monday to Friday | 9am to 5pm (AEST)
Monday to Friday | 9am to 5pm (AEST)
 Singapore
Singapore Philippines
Philippines India
India Australia
Australia Singapore
Singapore Philippines
Philippines India
India